
Introduction
With an increasingly hybrid workforce, securing endpoints should be a top priority for everyone. Due to the prevalence of the Windows operating system footprint in business environments, Windows endpoints continue to be a top target for attackers attempting to gain initial access to an environment. Many organizations are so hyper-focused on the latest network security tools, anti-malware and security monitoring solutions that they neglect to see a “low-hanging fruit” opportunity to secure the most vulnerable assets, user endpoints.
Windows operating system, currently Windows 11, has matured significantly when it comes to security. Many security features are now enabled by default, right out of the box, which helps raise the bar for home users and small businesses who might not otherwise know what atures or configurations to enable. That said, there is still much more that can be done to harden a Windows endpoint from attacks.
Getting Started
While there are many third-party tools and companies providing solutions for Windows endpoint security, I’m going to focus on native Microsoft tooling in this article as many of these tools are considered “free” or part of an organizations existing, base Microsoft 365 licensing. All the solutions mentioned here have the capability to be managed, at-scale, using device management tools such as Microsoft Intune or Windows Server Active Directory, or deployed individually on devices for smaller organizations just getting started.
Windows Update for Business (WUfB)
Microsoft’s modern approach to patching Windows endpoints in the business computing world, WUfB, replaces earlier solutions such as Windows Server Update Services (WSUS)or Microsoft Configuration Manager Software Updates. Unlike the previous solutions, WUfB relies on policies to control when Windows devices obtain and install quality and feature updates for the Windows operating system. Policy driven update deployment takes the hones off the IT administrator for manually approving updates as they are released and also provides more accessible update delivery mechanisms that ensure devices receive updates regardless of their current physical or network location.
Windows Update for Business policies can be enabled using device management tools such as Microsoft Intune, group policy in Windows Server Active Directory, or be manually configured on standalone Windows devices. Ensuring Windows Updates are configured and monitoring for compliance is one of the simplest actions any organization can take to further bolster their Windows endpoint security.
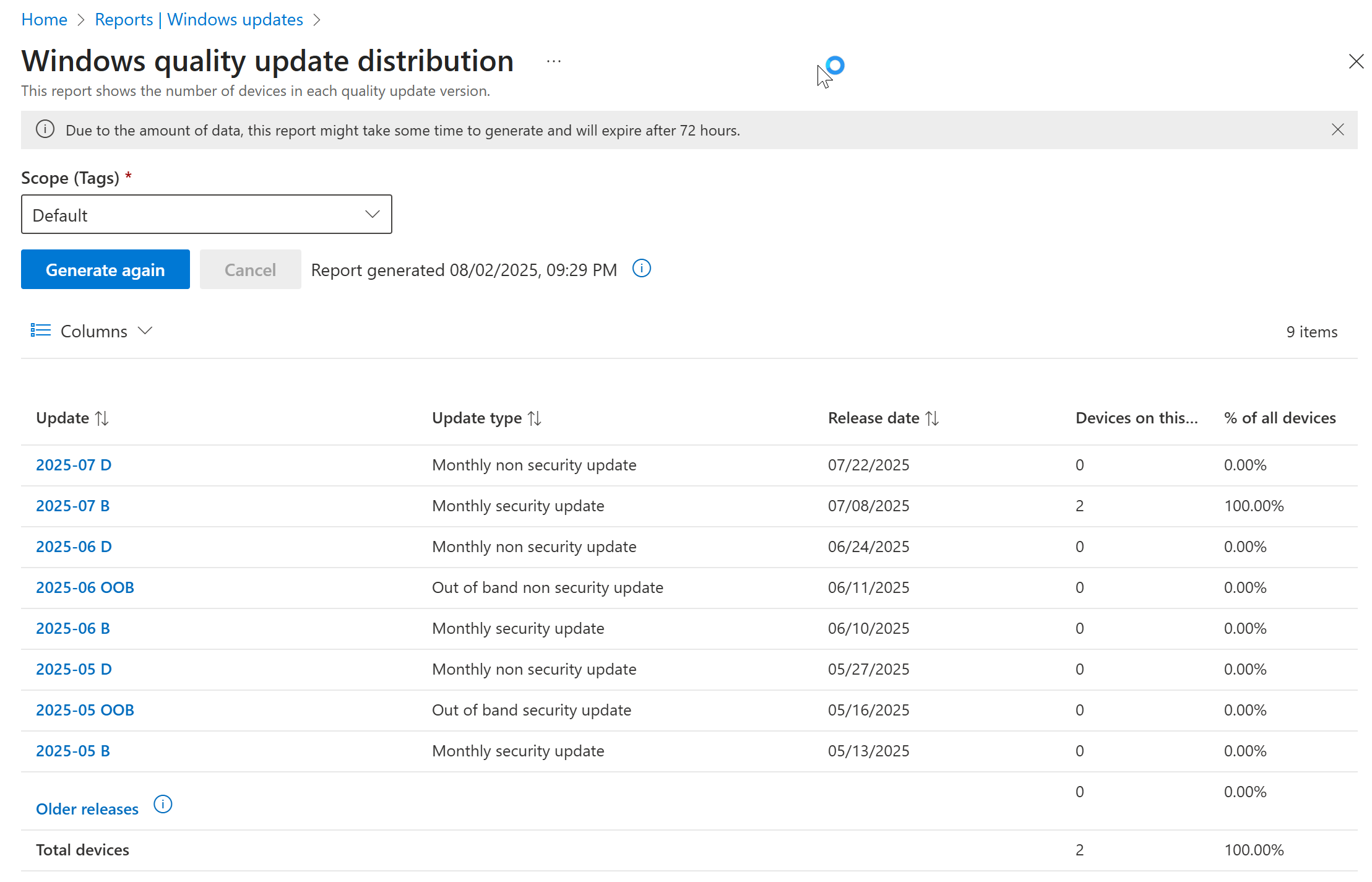
BitLocker
Laptop, or portable computers, make up approximately 80% of the number of new computers sold. How do you ensure that if a device is lost or stolen the information stored on that device is protected from prying eyes? BitLocker drive encryption is the Microsoft answer.
BitLocker functionality is included with all Windows 10/11 operating system versions and can be enabled manually or via management tools such as Intune or Windows Server Active Directory group policy (centralized management requires Business, Education or Enterprise versions of Windows). The benefits of managing BitLocker centrally include centralized escrow of recovery keys, automatic recovery key rotation and even user-driven recovery key retrieval. BitLocker compliance can also be monitored with modern device management tools such as Microsoft Intune.
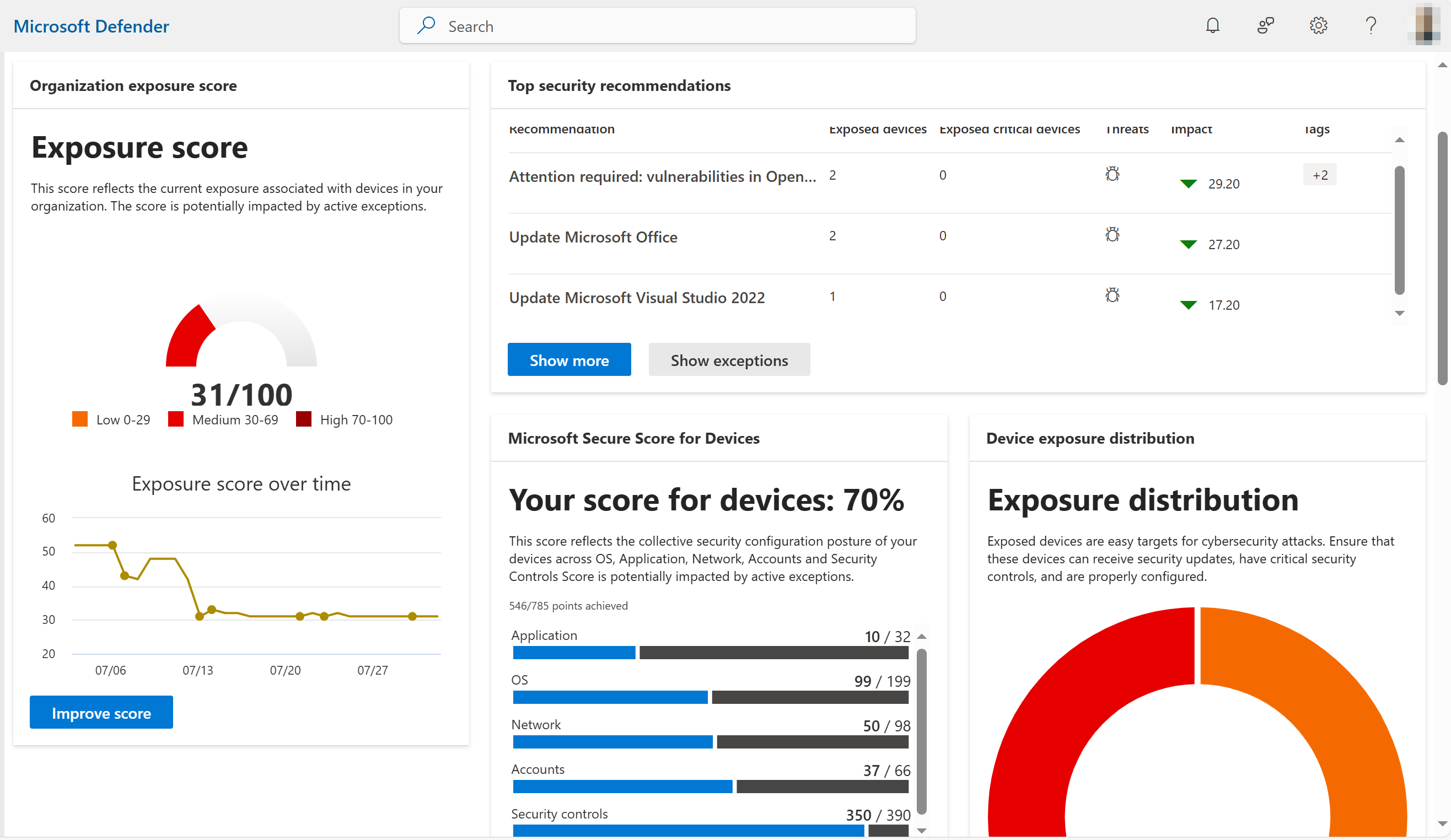
Windows Defender Antivirus/Defender for Endpoint
It’s common knowledge that antivirus on Windows endpoints is a must these days. While there are many third-party Windows antivirus/antimalware solutions on the market many organizations, and most home users, place their trust in the default protection built into the Windows operating system, aptly named Windows Defender Antivirus. While some in the industry, who usually have been around for some time and have pre-conceived notions of Microsoft security, may crinkle their nose at the mention of Defender Antivirus, the solution has a proven track record of excellence for detecting antimalware.
No antivirus solution is going to be perfect. In fact, often combining multiple antimalware solutions proves best in testing labs, however, that is not typically an achievable solution for many. What is readily achievable would be to extend the protection of Windows Defender Antivirus by enrolling the device in Microsoft Defender for Endpoint (DFE). DFE enhances device protection by enabling modern threat and vulnerability (TVM) management and endpoint detection and response (EDR)capabilities for situations where endpoints are compromised without the use of viruses/malware. Versions of Defender for Endpoint come with many of the base Microsoft 365 subscriptions for business and can even be used in conjunction with third-party antivirus solutions.
Windows Security Baselines
While many security protections are now enabled by default in Windows, there are additional configurations that can be enabled to further harden a device. These protections are not enabled by default as some may require the functionality the configuration is disabling, often in legacy environments or where certain computing scenarios are warranted (Internet connection sharing with a tethered mobile phone).
To get started with Windows endpoint hardening, Microsoft provides templates made up of settings/configurations that are considered “industry recommended”. The templates are meant to serve as a starting point and will require thorough review and proper deployment piloting to ensure day-to-day user productivity is not impacted. The templates can be downloaded and deployed using Windows Server Active Directory group policy (latest version 24H2 can be found here: https://www.microsoft.com/en-us/download/details.aspx?id=55319) or via solutions such as Microsoft Intune where management, versioning and updates can be orchestrated over time.
According to industry stats, deployment of security baselines for Windows can lead to 40% faster compliance audits and 30–50% fewer device misconfigurations.
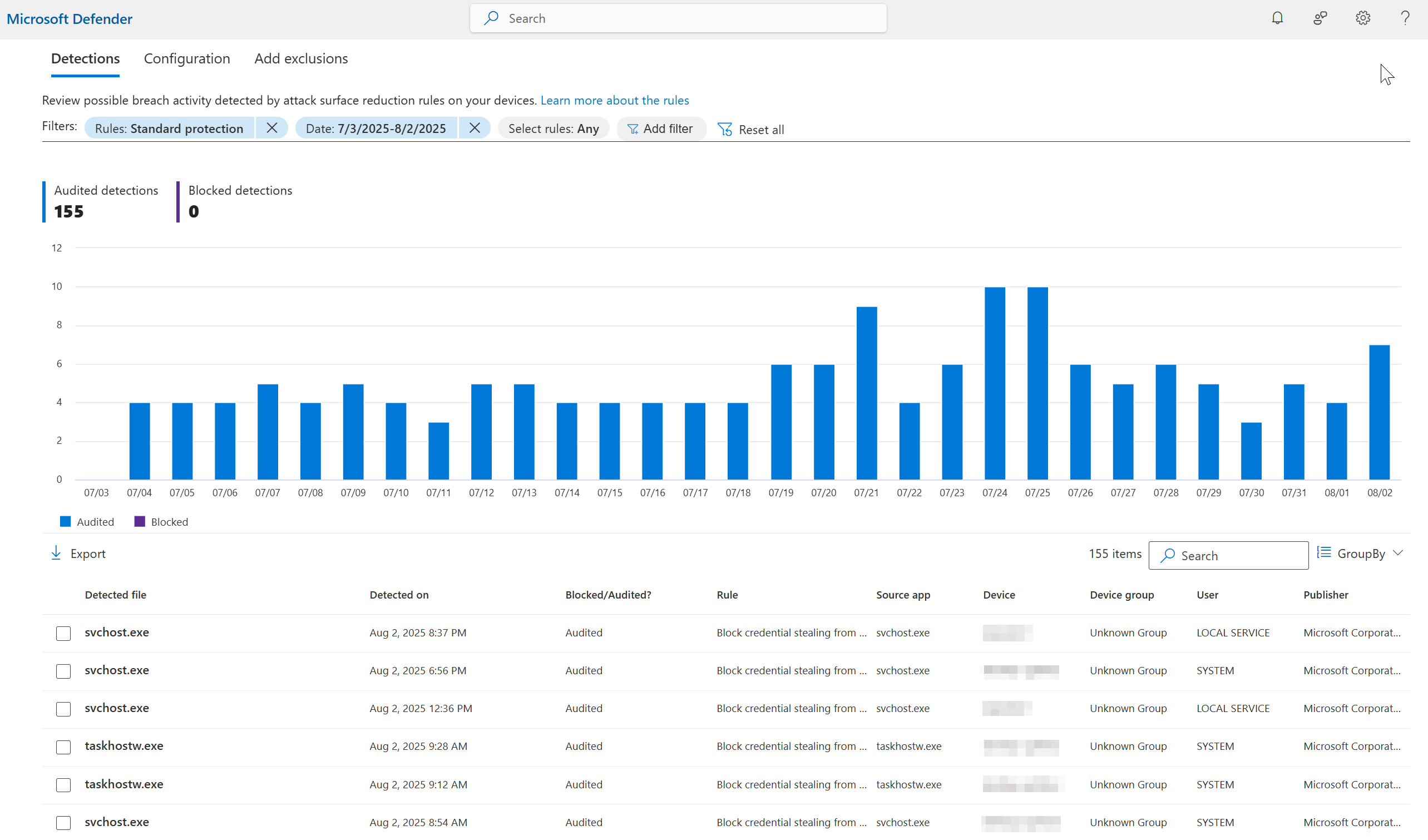
Attack Surface Reduction Rules (ASR)
Similar to Windows Security Baselines, Attack Surface Reduction rules are configurations that can further strengthen security on Windows devices. The key difference is that ASR rules target Windows Defender instead of the Windows operating system configuration. An example rule: Block all Office applications from creating child processes. This rule prevents Office apps like Word, Excel, and PowerPoint from launching other processes—such as PowerShell or cmd.exe—which is a common tactic used in malware attacks and phishing campaigns. Windows Defender is the safekeeper ensuring if this event is detected, it is blocked.
Similar to the Security Baselines, it’s critical to roll out ASR rules after thorough evaluation and proper piloting as some settings can have adverse impacts on user productivity (inhibiting Office macros).
Windows LAPS
The ability for an attacker to move laterally across devices in an environment is key to their success in elevating privileges. One of the easiest ways to stop lateral movement on a network is to not use the same username/password for privileged local user accounts on Windows endpoints. What does this mean?
If you deploy multiple Windows devices on a network with the same local administrator password and one device is compromised, it’s extremely likely that the attacker will use the compromised local administrator password to login to other devices on the network until they find a target device containing more privileged access or a more privileged account (escalation).
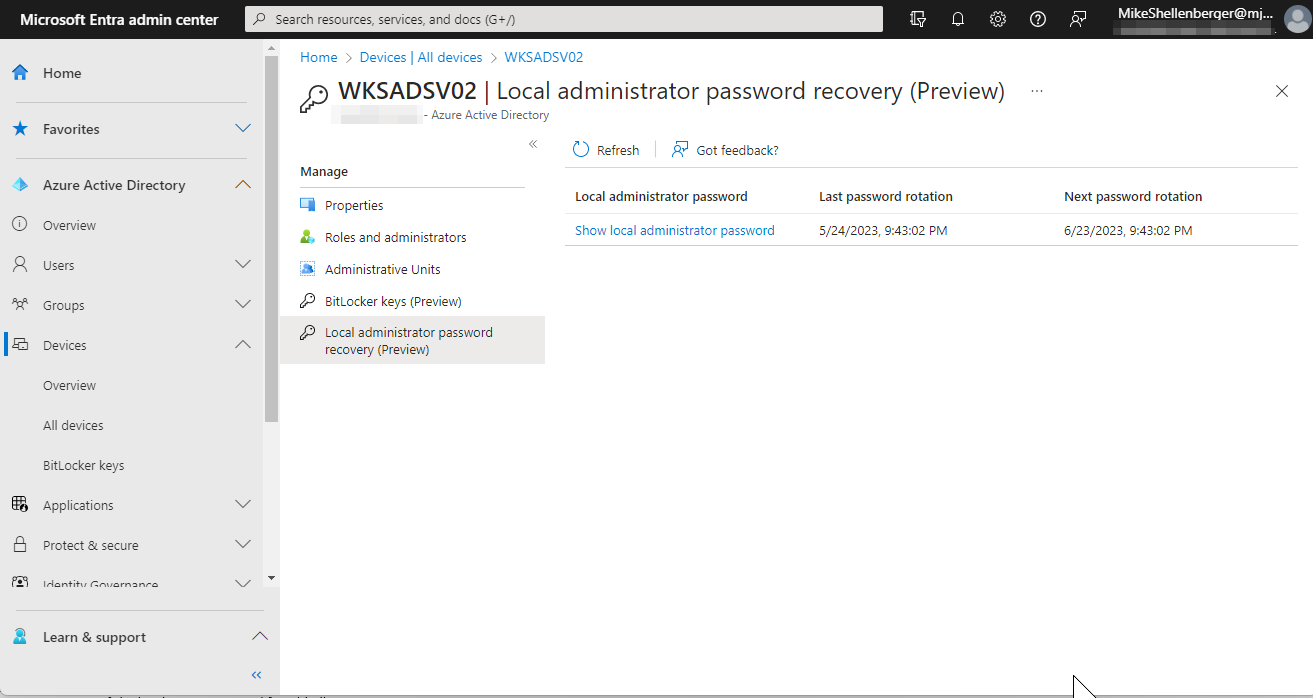
For organizations with tens, hundreds or thousands of Windows endpoints, this presents a challenge as accounting for different administrator passwords on each device is difficult, if not impossible. Employees within Microsoft realized this many users ago, and a pseudo solution named Microsoft LAPS (Local Administrator Password Solution) was developed as an add-on for enterprises using Windows Server Active Directory. The solution would create a unique local administrator password for a device, set the password, then escrow the password to a hidden attribute in Active Directory for retrieval by authorized individuals in IT, as needed.
While Microsoft LAPS was a great solution, the industry’s movement towards hybrid-work, mobility, and Entra joined Windows devices presented problems for Microsoft LAPS as it is reliant on Active Directory. Microsoft has since re-keyed the solution, naming it Windows LAPS, and has built the solution into Windows 10(April 2023) and later operating systems.
Windows LAPS capabilities have been expanded to include functionality such as automatic rotation of the password if the password is used, encrypted passwords in Active Directory, and password escrow to Microsoft Entra/Intune where it can be more readily accessed by authorized IT resources. Windows LAPS is a “free” solution, only requiring initial configuration on endpoints to get started.
Windows Hello for Business
Multifactor authentication (MFA) has proven to be a game changer in the advancement of protecting user identities. Passwords have long been regarded as insecure as they are easily guessed, attacked or stolen when poor password hygiene is used. MFA introduces a second form of authentication as it requires “something you have”. Usually this is in the form of an MFA app running on a smartphone in your possession or perhaps a USB hardware token that you plug into your device when logging in.
While MFA has been part of Azure Active Directory (now named Entra ID) for quite some time and is able to protect any cloud-based applications or resources integrated with it, the authentication process to log into a Windows device has remained password only. Intro Windows Hello, a way to perform strengthened logins to a physical Windows device.
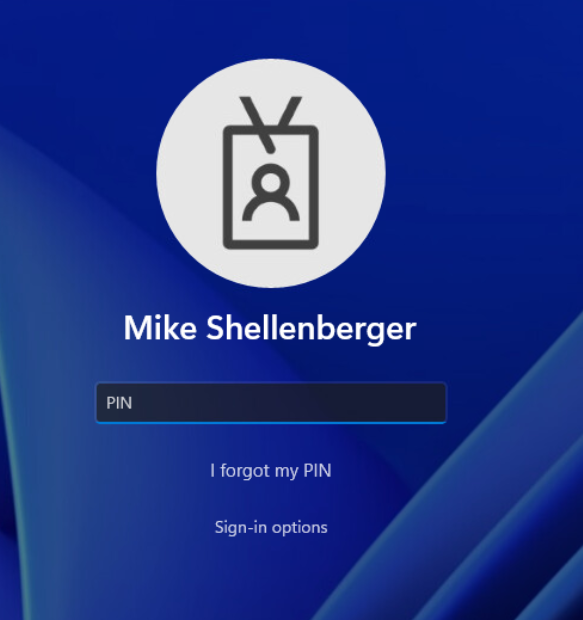
Windows Hello for Business takes advantage of biometrics capabilities, such as a fingerprint sensor or facial recognition camera, to authenticate a user. If a biometric capable authentication device isn’t present, a simple PIN code can be leveraged to login to Windows. Windows Hello for Business requires a user to be in front of the device and provide something they have, meeting strong identity requirements. Windows Hello for Business authentication cannot be used to login to devices across the network, making it secure from network-based attacks.
The authentication process for Windows Hello for Business stays local to the device and a password is never exchanged over the network. This further increases the security of the authentication process as it’s impossible for an attacker to steal credentials if they are monitoring the local network traffic.
Windows Hello for Business also provides the benefit of a smoother authentication experience for users. Simply sitting in front of the computer (facial recognition), providing their fingerprint, or providing a PIN code logs the user into Windows and a password does not need to be remembered or provided. Deploying Windows Hello for Business is simple if leveraging tools like Entra ID and Microsoft Intune and only slightly more complex to configure in a hybrid or all on-premises environment.
Routine Operational Review
So, maybe you have a few or all the aforementioned solutions deployed. What’s next for you? Creating a game plan to regularly review the configuration settings and latest policy versions is critical to staying protected. Features in Windows change, and when they do, new security baselines, attack surface reduction rules, defender antivirus settings, etc. are also released. Keeping on top of any new settings and regularly reviewing the environment to confirm if organizational needs have changed requires diligent planning and regularly scheduled events, to ensure protections stay current. I often recommend to my customers that they meet quarterly to review the environment policies, address any changes and explore any new security protections made available.
Keeping detailed documentation on security policy settings, in addition to the WHY, is extremely important. For the sake of all of those who may come after you to pick up the IT admin reigns, details as to WHY a setting was deviated from the default is crucial to avoiding mystification. Any changes made to policy should also note who made they change and provide a timestamp.
Next Steps
I hope this article has been helpful to unveil some of the native tools and solutions available to harden Windows endpoints. While many of these solutions are not difficult to deploy or configure, there is an advantage to having experience with deploying these policies and configurations. Instrumental knowledge of common rules and configurations that can cause strife for user productivity when deployed, based on experience, can play a key role in a smooth, expedited rollout. Lightspire Technologies has experience in deploying all of these Windows endpoint hardening techniques in many different size environments, industries and customer verticals. Please reach out to us if you would like to have a conversation to determine if Lightspire is a fit to work with you on your Windows endpoint hardening journey. You can learn more about Lightspire's Windows Endpoint Hardening services here.
Let’s Clarify Your IT Strategy
Unlock the full power of Microsoft to elevate your business. Let’s build smarter, faster, and more secure solutions—together.




